Zero Trust Security Solutions
Fill in your zero trust blind spots in Kubernetes and the cloud
Has the shared service model led to a proliferation of identities and permissions across Kubernetes and the cloud? Could your zero trust strategy prevent insider threats in Kubernetes?
RAD Security shows permissions and where they are used, as well as enforces least privilege access in your critical cloud infrastructure.
Manage your zero trust strategy across Kubernetes and the cloud
Detect insider threats to your zero trust model
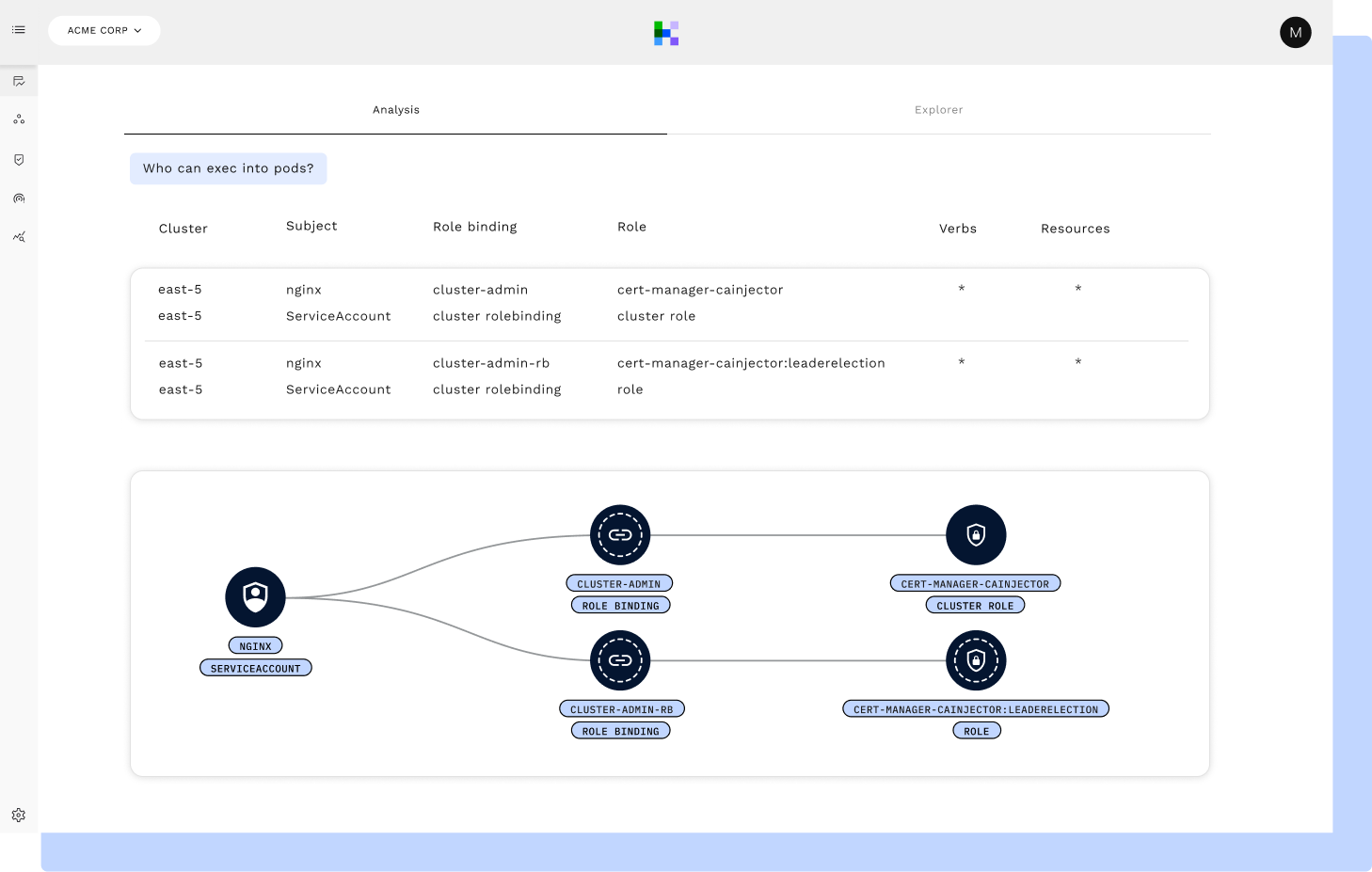
Malicious insiders with compromised, valid credentials constitute the most costly attack vector in a breach. But lists of over permissions from legacy KSPM and CNAPP providers don’t show the usage of valid permissions. RAD Security uses AI to comb through cloud metadata and audit logs, efficiently surfacing how permissions are actually used in order to detect malicious insiders.
Manage zero trust from Kubernetes to the cloud
Many zero trust initiatives have a large gap around Kubernetes and the cloud, risking non compliance with customer’s security requirements. RAD Security shows where least privilege issues are being exploited in the attack path from cloud IAM authentication to RBAC authorization.
Prioritize and address top cloud native identity risks
RBAC and Cloud IAM are often viewed as separate, large lists of misconfigurations, with little context or prioritization based on their association to other risks on the same workload. RAD Security connects RBAC and Cloud IAM issues to other cloud and Kubernetes misconfigurations, network issues, runtime alerts and image CVEs for a clear understanding of priority and impact.
Learn how with threat vectors
Enforce your zero trust framework with guardrails
Implementation of a zero trust model requires a successful partnership with engineering in the shared service model, enforcing policies that limit the proliferation of risky over permissions. RAD Security provides Kubernetes-native guardrails and remediation guidance down to the manifest code, encouraging effective understanding and collaboration with engineering.
Learn why SREs should care about Kubernetes security
RAD Security uses AI to detect anomalies in cloud native identity, while prioritizing over permissions with broad context, so you know where and how to enforce least privilege access with Kubernetes native guardrails
Zero Trust across Kubernetes and the Cloud
Start with the identity inventory for your riskiest identities
Use AI to understand actual activity across your audit logs
Prioritize over permissions by their relationships to other risks
Threat vectors show the top risk across a broad set of Kubernetes components
Right-size Kubernetes RBAC permissions
Streamline the implementation of least privilege access

