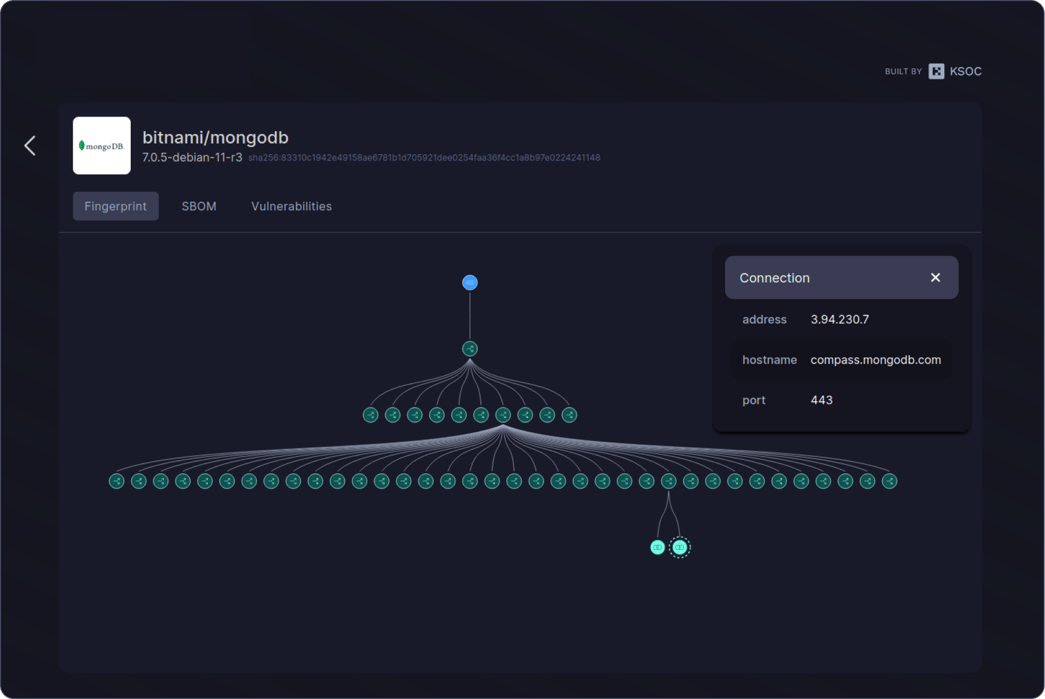
What is RAD security?
The RAD security standard uses eBPF to codify the baseline behavior of a cloud workload into a behavioral fingerprint, so DevSecOps teams have a transparent, verifiable defense against the next wave of zero day software supply chain attacks.
Use-cases
Software Supply Chain Security
Behaviors captured and analyzed by eBPF form a unique, verifiable fingerprint that can be used throughout the SDLC to ensure integrity
Zero Day Detection
Use a verifiable fingerprint of cloud workload behavior for a ground zero representation of what should be running in your environment
Runtime Security Fingerprints
Verified runtime security fingerprints via a light-weight eBPF agent make automated, contextual response actions possible and lower false positives by 99%