Intro
As Kubernetes continues to grow in adoption, security teams are still struggling with adapting security to ephemeral, cloud native environments. In this blog, we will address KSOC’s further capabilities, following the recent release of threat vectors and real-time KSPM, to help security teams cover their blind spots. Included in this release are cloud native identity threat detection, cloud compliance, AI-guided auto-remediation, CVE exploitability and more.
Why security teams are still struggling to adapt to ephemeral, cloud native environments
Cloud native security from the inside-out
Cloud native identity threat detection
Prioritize CVEs with CVE Exploitability
Easier Security Administration with Resource Tagging
Why security teams are still struggling to adapt to ephemeral, cloud native environments
While the number of cloud native security vendors has proliferated, security practitioners are still struggling to efficiently adapt security to the new reality of their cloud native environments. In some organizations, Kubernetes represents the entirety of the cloud deployment, and recent research shows that 90% of Kubernetes deployments are on the cloud versus on-premises. As engineering has put Kubernetes front and center in its cloud native migration, security efforts for these new environments have been left behind.
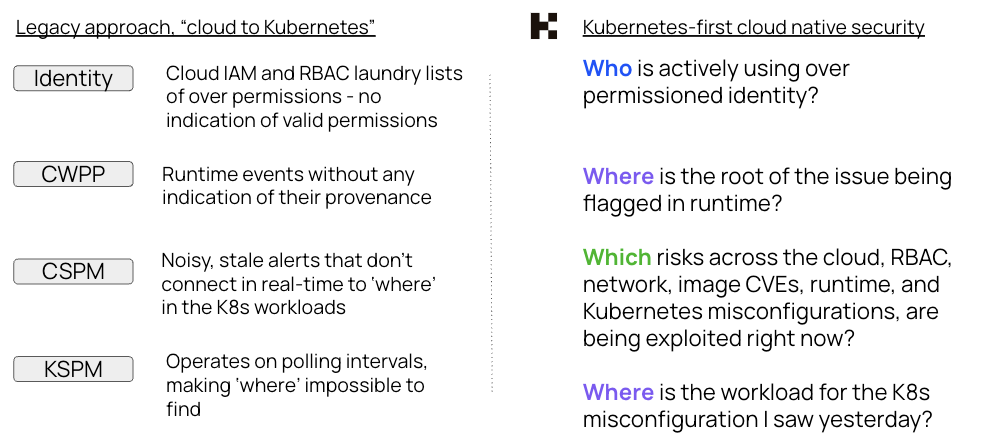
While container security and Cloud Service Posture Management (CSPM) tools have their benefits, as the adoption of Kubernetes grows, these approaches to securing a Kubernetes environment limit security teams in multiple ways, by:
- Relying on misconfiguration scanning that doesn’t take into account the Kubernetes lifecycle
- Using either limited admission controllers, or ones that are not Kubernetes-native in their deployment or usage, often sending images or unnecessary data to the vendor’s cloud
- Showing noisy lists of over permissions instead of actual usage of valid permissions, despite the fact that, in Kubernetes and the cloud, malicious insiders and valid credentials represent the most common, costly attack vectors
- Botching the connection of Kubernetes components together, leaving Kubernetes itself either out of the picture entirely, or failing to connect it in real-time to the various cloud services and container or CI/CD processes it directs
With all of these issues, infrastructure security engineering teams are left with multiple blind spots and extra work they don’t have time to do. In short, the legacy approach of securing a Kubernetes environment leaves teams struggling to adapt security to their ephemeral cloud native infrastructure.
Kubernetes-first cloud native security
To give security teams a better option for adapting security to their Kubernetes environments, KSOC maps the broad components of your cloud infrastructure in real-time for accurate cloud native identity threat detection, risk and incident detection.
Compared to legacy solutions, we include ephemeral workloads in the prioritization process, allowing us to provide more accurate detection, response and remediation guidance, along with insight into the actual usage of cloud native permissions in both RBAC and the cloud. For busy security and engineering teams, this approach is more efficient and accurate, with an option for broad consolidation of tools and vendors.
Learn more about Kubernetes-first cloud native security
Addressing ephemeral cloud native environments with threat vectors and real-time KSPM
KSOC’s threat vectors map the various components of Kubernetes in a real-time graph to understand, based on broad context, which are the top priority risks and incidents. See how it helps prioritize a broad set of vulnerabilities in this video:
Real-time KSPM allows threat vectors to achieve better accuracy and detection, ensuring that any misconfigurations represent the actual state of the cluster, versus the state of the cluster two hours ago, or whenever the last polling interval took place. Imagine trying to locate a workload with a misconfiguration, and it has already been deleted . . . this is the reality without real-time KSPM.
Introducing cloud native identity threat detection
Threat vectors and real-time KSPM are just the start for what teams need to effectively address security for their ephemeral cloud native environments, including complying with regulations like NIST / SOC / PCI. Due to the shared service model, where containerized, distributed workflows allow for different teams to spin up cloud IAM and Kubernetes RBAC roles independently, we are seeing a broad increase in insider attacks and other breaches caused by the proliferation of credentials and identities.
- Three of the four Kubernetes-targeted attacks this year took advantage of over permission RBAC policies.
- According to the recent cost of the breach data from IBM, malicious insiders are the single most costly initial attack vector
- Stolen or compromised credentials are the second most common initial attack vector malicious use of valid credentials
- Breaches initiated with stolen or compromised creds and malicious insiders took the longest to resolve, compared to alternatives like phishing or exploitation of zero day vulnerabilities
Despite the criticality of cloud native identity, today, CSPM and open source RBAC tools fall short of identifying malicious activity. The most common approach to this problem today applies the tactics used in a classic CSPM or image scanner, by creating lists of RBAC over permissions but don’t include context to determine the relative importance, or actual usage, of over permissioned identities. This legacy method leads to noise and can even fray the relationship between security and engineering, as security tries to change policies that engineering has set without a full understanding of the policies’ impact on the overall security posture.
To address these issues, KSOC’s new cloud native identity threat detection platform includes the following capabilities:
- Attack paths between Cloud IAM and Kubernetes RBAC
- Find risks in the interaction of Cloud IAM and Kubernetes RBAC
- Cloud native identity anomaly detection
- View actual usage to find Malicious insiders and other attacks utilizing valid or overly permissive credentials
- Baseline ‘normal’ RBAC behavior and detect anomalies using AI to query cloud metadata, RBAC configurations and Kubernetes API audit logs
- Top priority RBAC and IAM misconfigurations
- Prioritize the most critical configurations based on the connections between RBAC permissions, Kubernetes misconfigurations, network exposure, runtime alerts and image CVEs on the same workload
Here is an example of AccessIQ, KSOC’s new easy audit log AI query capability, that shows which credentials are being used to access resources, versus just which over permission exist, but may or may not be used today:
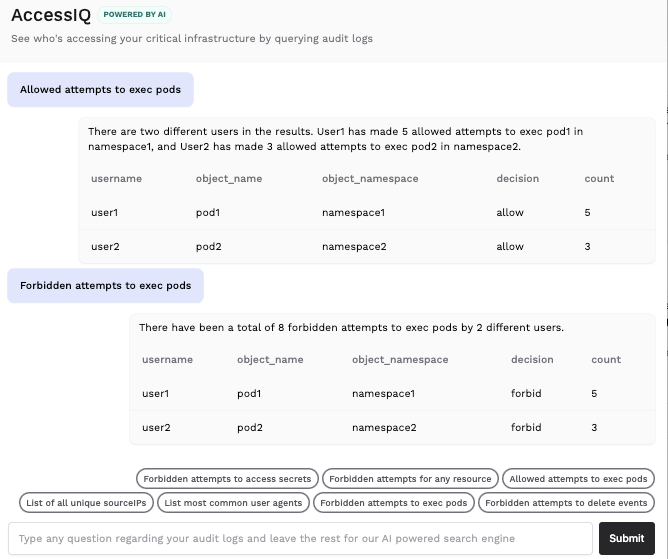
Cloud native identity is the perfect use-case for the application of AI, the usage of which has been found to cut the time to contain a data breach by 108 days (versus those organizations that don’t use security AI and automation). In the case of identity, not only is AI helpful for combing through large amounts of data to find patterns, it also makes it easier to interrogate logs at scale to detect novel attacks or patterns because of the natural language processing in the query process, speeding further development of the capability.
AI-powered auto-remediation
To speed up the time to remediation for the misconfigurations in your environment, we are also announcing a new AI-powered remediation capability that provides the actual, suggested changes in your manifest code. See it in action here:
EKS cluster discovery
With KSOC, you can discover the clusters in your EKS environment, with instant visibility into the clusters that are not currently secured by KSOC. See the capability in action here:
Cloud compliance
KSOC is now offering compliance checks across more than 20 compliance frameworks, encompassing recognized standards such as:
- CIS (Center for Internet Security)
- FedRamp (Federal Risk and Authorization Management Program)
- HIPAA (Health Insurance Portability and Accountability Act)
- NIST (National Institute of Standards and Technology)
- SOC2 (System and Organization Controls 2)
...and many more
Here you can see the full list of frameworks and compliance across the board. See this quick video:
Find the next log4j for free with our searchable SBOM
We all remember log4j and the all-encompassing aftermath. Finding the relevant packages, understanding whether they are actually running or not in order to prioritize patching, re-factoring code where necessary, etc. For instances like this, KSOC allows you to create and search an SBOM of all your running images for a specific package name. We will show all running packages . . . not just all packages in all registries. This can lower the overall amount of effort required, since you know what should be prioritized as a part of your actual, running environment.
Prioritize CVEs with CVE exploitability
Vulnerability management in a cloud native environment is so hard because there are simply too many vulnerabilities and not enough people to address them. KSOC is announcing the ability to see which of your CVEs are in-use in your running environment, so you can better prioritize which ones to fix first. This capability is possible through the combination of eBPF runtime data and the cluster images.
See this video for a short walk-through!
Easier security administration with resource tagging
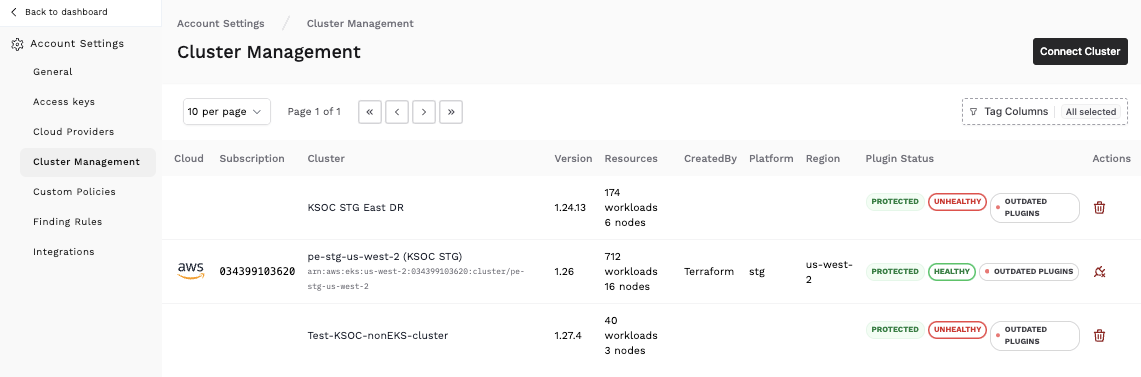
Every Kubernetes environment is different; with KSOC’s new resource tagging capability, you can easily tag a cluster according to your own organization’s labels. This means you can easily pair a finding to the appropriate team for remediation, show your top risks and threat vectors in your own internal terminology, ignore findings from particular resources, and much more!
In this example, you can see the tagging for an EKS cluster by a tag indicating the provenance of the cluster, the platform and the region.
PING identity SSO
Now, SSO into KSOC seamlessly if you are using Ping identity. You can now add KSOC to your list of apps you can SSO into using Ping
Conclusion
KSOC is the only vendor to take an approach to cloud native security that is Kubernetes-first, from the inside out, giving you a unique view of your risk in real-time. With these new additions to the real-time platform, you can take a step further in stopping your top attack vector, providing accurate remediation guidance, and improving efficiency by prioritizing and searching for relevant risks.
For more information on KSOC’s real-time platform, reach out to the team today!



